Your own email: Great power comes with great responsibility
There are days that you do things out of the ordinary. That day, I opened my spam folder…exceptional behavior for all of us. This is not the end, I found a self-sent threatening email. That’s me, a proper villain :)
This amazing finding set off a thought process in my head.
How? How is it possible?
Let’s dig in and start a little investigation!

DNS records theory
We will start with the theory to be on the same page. You will know what defends our identity and provide sender verification.
What is the SPF DNS record?
Sender Policy Framework (SPF) is a simple email-validation system designed to detect email spoofing by providing a mechanism to allow receiving mail exchangers to check that incoming mail from a domain comes from a host authorized by that domain’s administrators1.
What is the DKIM DNS record?
DKIM (DomainKeys Identified Mail), allows senders to associate a domain name with an email message, thus vouching for its authenticity. This is done by „signing” the email with a digital signature, a field that is added to the message’s header. The recipient MTA can verify the DKIM signature, which gives users some security knowing that the email did actually originate from the listed domain and that it has not been modified since it was sent1.
What is the DMARC DNS record?
DMARC (Domain-based Message Authentication, Reporting, and Conformance), is an email authentication standard, policy, and reporting protocol. It builds on the widely deployed SPF & DKIM protocols and is the only way for email senders to tell email receivers that the emails they are sending are truly from them. Using DMARC enables senders to publish a policy on how email servers should react to inauthentic messages1.
My DNS configuration
Previous
Yeah…it looks kind of poor. I thought one record with a loose policy would keep me safe. As you can see below, „~all” states that unlisted emails will be marked as insecure or spam, but still accepted.
v=spf1 ip4:<OTHER_MAIL_SERVER_IP> include:_spf.google.com ~allCurrent
What changed? Now SPF record has a „-all” statement, which tells the server that addresses not listed in the SPF record are not authorized to send emails and should be rejected. Besides that, the DKIM record provides a public key and every message sent from my addresses is signed and can be verified by the receiver.
Last, but not least, the king of „email records” DMARC. The most restrictive configuration you can imagine!
p=reject, which instructs email servers to block emails that fail DKIM or SPF for the main domainsp=reject, which instructs email servers to block emails that fail DKIM or SPF for subdomains
v=spf1 ip4:<OTHER_MAIL_SERVER_IP> include:_spf.google.com -allv=DKIM1; k=rsa; p=<public_key>v=DMARC1; p=reject; sp=reject; rua=mailto:<ID>@dmarcinput.com; ruf=mailto:<ID>@dmarcinput.com; fo=1DMARC Report Tool
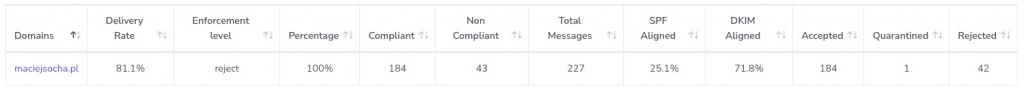
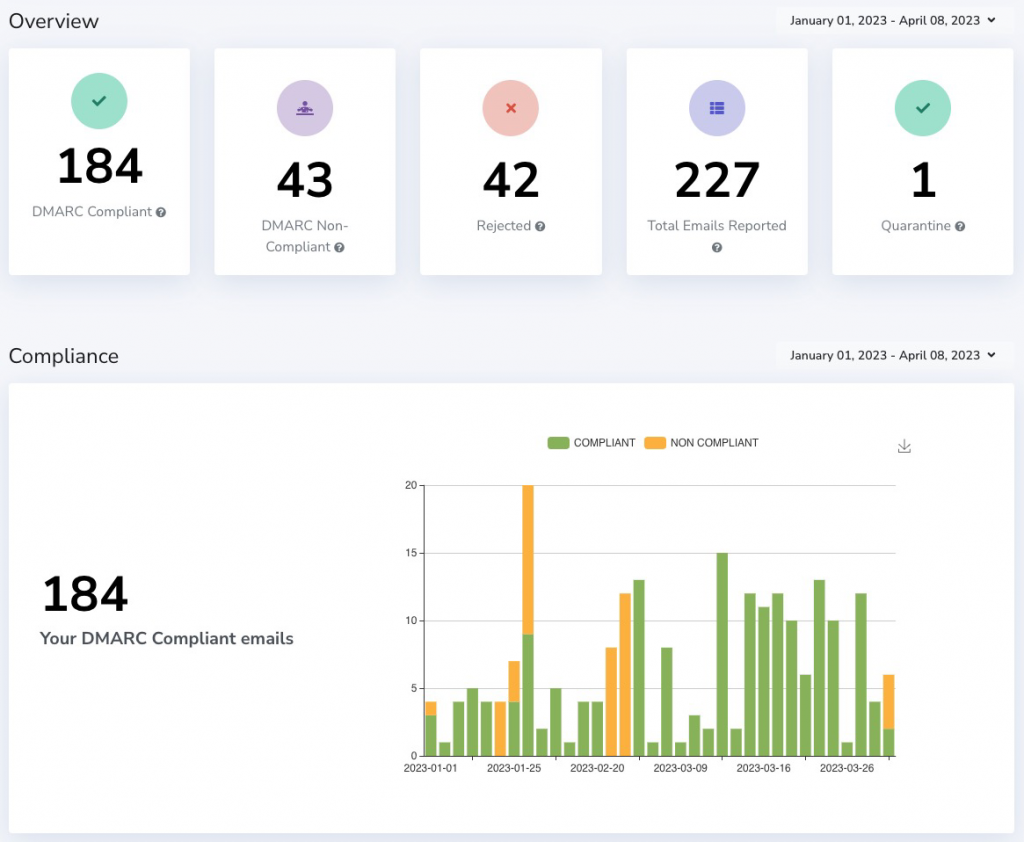
Your configuration is in place, but how can you verify if it helped? Report Tool, that’s the answer. I recommend DMARC Report, the free tier will be more than enough for personal use. Statistics are presented in easily readable forms of graphs and tables.
Let’s check the last 3 months. 18.9% of emails sent as „me” were rejected by mail servers! That’s a lot of fake emails. They were sent from 8 different countries and from a dozen IP addresses.
Summary
We often neglect important details of our everyday tools. Those details lead to our online visibility and can be used as phishing tools as my email address. The situation I described above was not acceptable to me, so I took steps to change it once and for all.
I hope that the above text will make you a little more aware and you will secure your e-mail as I did.